Sometimes when an app is developed and released, the company behind it forgets that there is a world outside the United States and releases it to the US iTunes store only. So while everyone in the US is downloading the app and putting it through its paces, everyone in the rest of the world is frustrated that they can’t get their hands on it.
Apple doesn’t advertise this fact for obvious reasons, but no matter where you are in the world, you can have a US-registered iTunes account. The only drawback is that any credit card attached to the account must be a US one. So more than likely, you can only use your US account for free downloads.
Here is how to make your US iTunes account.
Make a US iTunes Account If You Are Outside The US
Open up iTunes and on the right hand side, there is a link which says “Account“. Click on that. Make sure first that you are logged out of all other accounts.
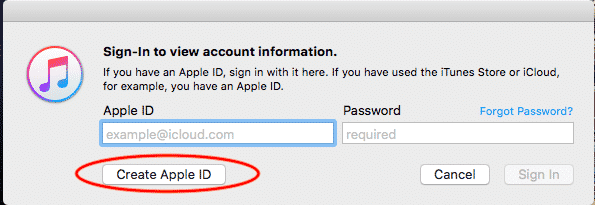
When the login box comes up, click “Create Apple ID”. If that button isn’t there, then it means you’re already logged into another account. Go back and log out of that account first.
Enter your email address, a password, and choose “United States” as your country. Tick the terms and conditions box, then “Continue” at the bottom right.
Apple probably wouldn’t approve of people doing this, so just to be safe, make a throwaway email address for this account. You don’t want to run the risk of compromising your main Apple account if they found out.
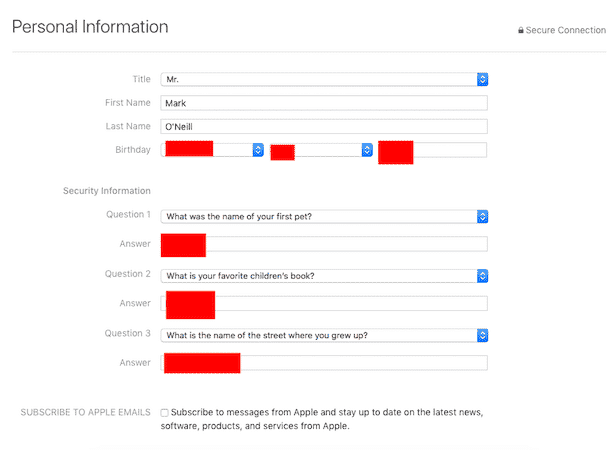
On the next screen, fill out the details. You may want to consider using a fake name (it won’t be checked by Apple). However, since this account is only for this article, and therefore will never be used, I just put my real name down.
OK, on the next screen, under “Payment Method“, choose “None“. This will make the payment method section disappear.
Then it’s time to leave an address. This is where you need to get creative. There are many places to get an address.
You will also need to enter a phone number. Just make something up.
You will then be told that a verification code is being sent to the email address you registered with. When the six digit code arrives, enter it and your account is active.
Now log in and start downloading that cool new app from Google.
One Drawback
One drawback I have found is if you are running two Apple accounts on your iPhone or iPad, then you can obviously only be logged into one account at a time.
This means if there are any updates for the apps downloaded under the other account, you won’t get them until you log out of one account and log into the other. A minor annoyance but nothing too serious. A toggle button for more than one Apple account would be nice, Apple.
Conclusion
On the one hand, I am not sure how much Apple would approve of people doing this. On the other hand, they could easily stop it with geoblocking non-US IP addresses. So perhaps they don’t care.
Either way, take precautions and don’t use any information tied to your main Apple account, the one with the paid purchases. Otherwise you may find both accounts shut down